

TeamViewer provides everything needed in the field of remote access and support, offering a reliable solution that increases productivity and customer satisfaction in the business world.
It allows users to remotely connect to another computer, mobile device, or server over the internet.


TeamViewer provides everything needed in the field of remote access and support, offering a reliable solution that increases productivity and customer satisfaction in the business world.
It allows users to remotely connect to another computer, mobile device, or server over the internet.

Remote Support and Access
- Instant Help: Technology experts can instantly resolve technical issues without any distance limitations.
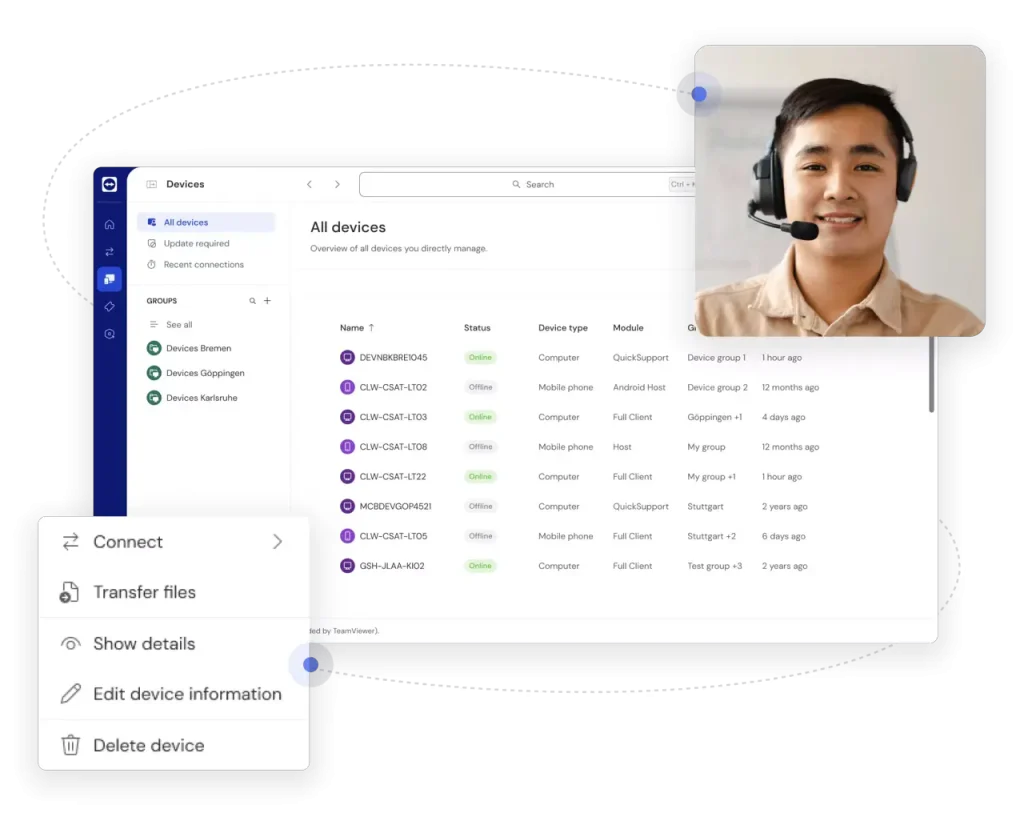
- Device Management: Provides remote access and control to any device, whether it's a computer, tablet, or smartphone.

Remote Support and Access
- Instant Help: Technology experts can instantly resolve technical issues without any distance limitations.
- Device Management: Provides remote access and control to any device, whether it's a computer, tablet, or smartphone.
Security:
- Encryption: Session data is protected with the most advanced encryption techniques.
- Two-Factor Authentication: A two-step verification system is used for additional security.
- Device Approvals:Secure device lists and strong password policies are implemented to prevent unauthorized access.


Security:
- Encryption: Session data is protected with the most advanced encryption techniques.
- Two-Factor Authentication: A two-step verification system is used for additional security.
- Device Approvals:Secure device lists and strong password policies are implemented to prevent unauthorized access.

Cross-Platform Compatibility:
- Multi-Operating System Support: Works on various platforms such as Windows, macOS, Linux, iOS, and Android.
- Web-Based Access: Users can access the system via a browser without installing any additional software.

Cross-Platform Compatibility:
- Multi-Operating System Support: Works on various platforms such as Windows, macOS, Linux, iOS, and Android.
- Web-Based Access: Users can access the system via a browser without installing any additional software.
File Transfer:
- Fast Transfer: Quickly and securely transfers files between connected devices.
- Secure Sharing: Transferred files are encrypted according to security standards.
Remote Management:
- Control Panel: Enterprise users can manage networks and devices from a central control panel.
- Automation: Updates, backups, and other management tasks can be automated.
- Reporting: Provides detailed reports on system activity, security, and device usage.

File Transfer:
- Fast Transfer: Quickly and securely transfers files between connected devices.
- Secure Sharing: Transferred files are encrypted according to security standards.
Remote Management:
- Control Panel: Enterprise users can manage networks and devices from a central control panel.
- Automation: Updates, backups, and other management tasks can be automated.
- Reporting: Provides detailed reports on system activity, security, and device usage.

